A Comprehensive Comparison Between Virtual Hosts and Subdomains
Virtual Hosts
Virtual hosts are websites running on multiple domains on the same physical server, and these units are independent of each other. They can have their own separate domain names, IP addresses, and website content, but they share the same server and operating system, as shown below:
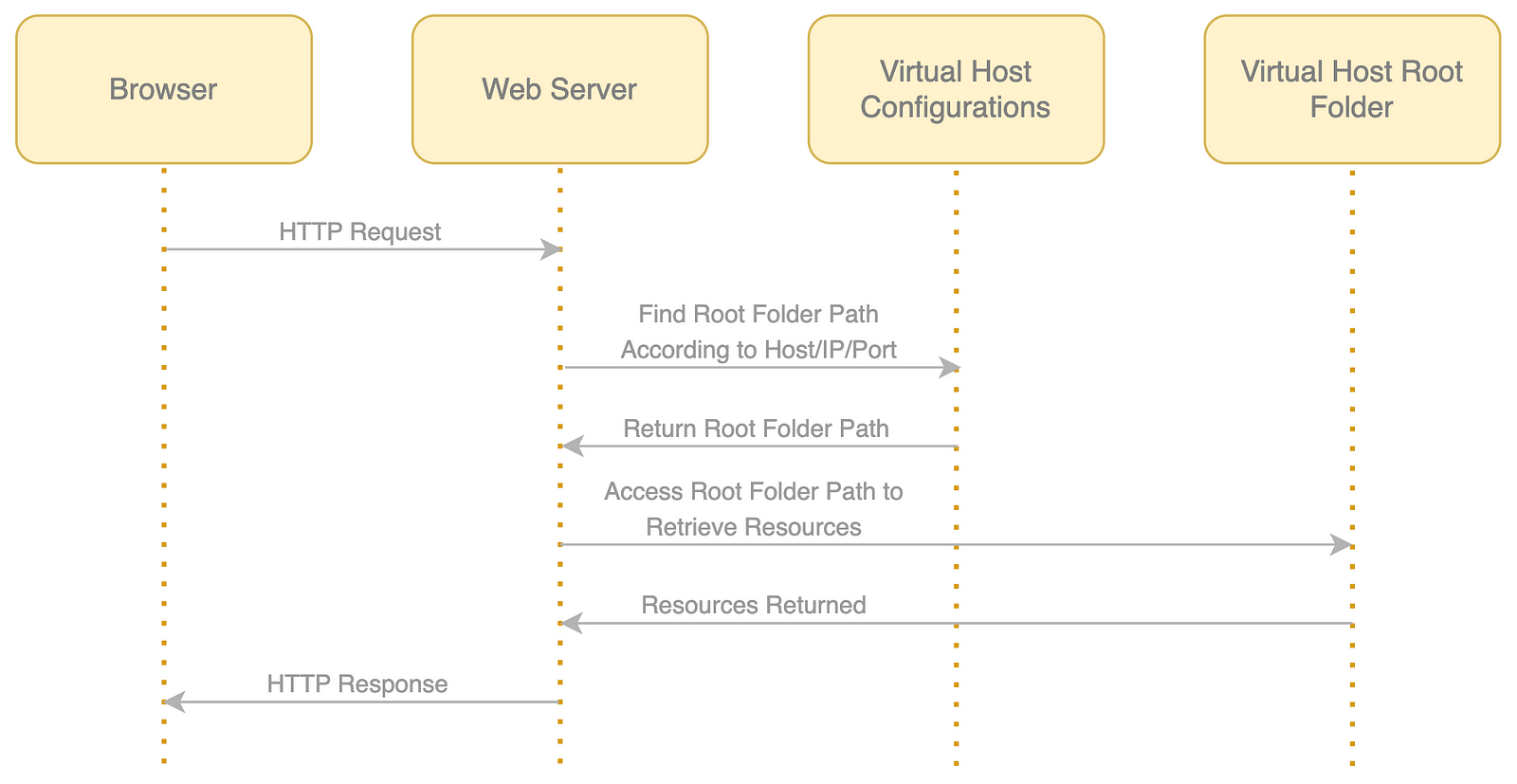
Web users can access a specific website by domain name, IP address, or port, as shown in the figure below:
Virtual hosts are typically used in the following scenarios:
- Hosting multiple websites with different domain names on a single server;
- Saving server resources and costs.
Types
There are 3 types of virtual hosts: 1) URL-based; 2) IP address-based; and 3) port-based, as shown in the table below:
| URL-Based | IP Address-Based | Port-Based | |
|---|---|---|---|
| Depending on Host Header | Yes | No | Yes - URL Used No - IP Addresses Used |
| Multi IP Address Requirements | No | Yes | No - URL Used Yes - IP Addresses Used |
| SSL/TLS Protocol Limitation | Yes | No | Yes - URL Used No - IP Addresses Used |
| Efficiency | High | Medium | Medium |
| Flexibility | High | Medium | Medium |
| Usability | High | Low | Medium |
| Security | Medium | High | Medium - URL Used High - IP Addresses Used |
DNS Resolution
Virtual hosting is implemented at the configuration level of a web server and allows multiple websites to be hosted on a single server. In the DNS resolution process, each virtual host usually corresponds to one or more domain names, and the DNS server resolves these domain names to point to the server with the same IP address. After receiving a HTTP request, the web server decides which virtual host’s content and resources to respond to the user based on the Host header in the request packet.
However, public DNS usually cannot resolve some virtual hosts, mainly because public DNS does not have the correct A record, AAAA record, or CNAME record, and these virtual hosts share the same IP address and run on the same physical machine. In this case, the only way to distinguish between different websites is through the Host header information in the HTTP request. If you need to access these virtual hosts in a browser, one way to achieve this is to manually add DNS resolution records in the /etc/host file (Linux) or in the C:\Windows\System32\drivers\etc\hosts file (Windows).
Potential Security Concerns
Misconfiguration
Misconfigured virtual hosts can cause websites with different domain names to leak each other’s sensitive information.
As an example, let’s say there is a web server with a public IP of 1.1.1.1 and hosting two websites example.com and a.example.com. Failure to properly distinguish between the directories corresponding to the two domains may result in a.example.com being accessed with the contents of example.com, or a.example.com being accessed with the contents of example.com.
Access Control Concerns
There may be access controls that are not properly configured, allowing unauthorized access to the contents of the virtual host.
In Apache, access control is usually configured 1) globally in the httpd.conf file, and 2) specifically in the configuration file corresponding to each virtual host (e.g., in the directory /etc/apache2/sites-available). The following are some of the settings in the virtual host configuration, where Order, Allow, Deny, etc. define the access control rules for the virtual host.
<VirtualHost *:80> |
In Nginx, similar to Apache, global configuration can be configured in the nginx.conf file, and a separate virtual host configuration file is located in the /etc/nginx/sites-available directory. As follows, the allow parameter in the location block defines the access control rules for the virtual host.
server { |
Therefore, the following considerations need to be taken into account in the access control definitions:
- Determine access requirements based on the business context and limit access to IP addresses with
AllowandDenyparameters; - Authentication mechanisms can be integrated into security controls if needed;
- Logging would need to be enabled to ensure that exceptions can be logged and regular log reviews are performed.
Virtual Host Enumeration
In general, URL-based virtual host is one of the most common practices, and we can use different tools for virtual host enumeration:
- Gobuster:
gobuster vhost -u http(s)://<TARGET> -w <WORDLIST_FILE> --append-domain - Ffuf:
ffuf -w <WORDLIST_FILE>:FUZZ -u http(s)://<TARGET> -H 'Host: FUZZ.<TARGET>' - Nmap:
nmap -p <PORT> --script http-vhosts <TARGET> - Nikto:
nikto -h <TARGET_IP> -p <PORT> -vhost <TARGET_URL>
Subdomains
After discussing virtual hosts, there is no mandatory requirement for subdomains to share the same server and operating system as virtual hosts do. Subdomains are subdivisions of the main domain name and are often used to distinguish between different services, departments, or geographic locations. Subdomains can be set up with DNS records (such as A records, AAAA records, or CNAME records), which can point to different IP addresses or different ports on the same IP address.
Subdomains are typically used in the following scenarios:
- Separating different services or departments under the main domain name;
- Providing different websites or services without the need for additional domain names.
DNS Resolution
A subdomain is a branch under the main domain name, which is usually used to separate different services, departments, or geographical locations under the main domain name. In public DNS, subdomains are usually available for resolution (i.e., A records, AAAA records, or CNAME records can be found.) In the DNS resolution process, the browser will find the corresponding IP address based on the DNS record, and then sends requests to that IP address.
Potential Security Concerns
- Unauthorized Access: Some subdomains may not be properly protected, which may result in the disclosure of sensitive information or unauthorized access.
- Subdomain Hijacking: If an attacker is able to tamper with DNS records or use DNS cache poisoning attacks, they are able to hijack subdomain traffic and perform malicious actions such as man-in-the-middle (MITM) attacks or stealing sensitive information.
Subdomain Enumerations
There are different tools we can use to enumerate subdomains:
- DNSEnum:
dnsenum --enum <TARGET> -f <WORDLIST_FILE> -r - Ffuf:
ffuf -w <WORDLIST_FILE>:FUZZ -u http(s)://FUZZ.<TARGET> - Amass:
amass enum -d <TARGET> - Assetfinder:
assetfinder --subs-only <TARGET> - DNSRecon:
dnsrecon -d <TARGET> - DIG Zone Transfer:
dig axfr @<NS_ADDRESS> <TARGET>
Conclusion
By learning about virtual hosts and subdomains, I have learnt that virtual hosts are a special type of subdomain. Virtual hosts require sharing the same server and operating system, and some domain names for virtual hosts are not resolvable in the public DNS. On the other hand, subdomains are able to get domain names resolved in public DNS easily.
A Comprehensive Comparison Between Virtual Hosts and Subdomains
https://wudiaries.com/2024/08/09/A-Comprehensive-Comparison-Between-Virtual-Hosts-and-Subdomains/





